What we know:
- A cyber-attack using a ransomware called WannaCry appears to have infected tens of thousands computers worldwide.
- The ransomware is demanding $300 USD per computer in Bitcoin to restore computer access.
- In the U.K., non-emergency patients are being turned away at hospitals until computer systems are restored.
- Computer security experts believe the ransomware spreads using a Microsoft flaw exposed in a recent leak from U.S. intelligence agencies.
UPDATE: In addition to confirmed cyberattacks in the UK and Spain, People’s Daily reports identical ransomware screens appearing in China.
A cyber-attack using a ransomware called WannaCry appears to have infected tens of thousands computers worldwide. In as many as 74 countries, including UK, US, China, Russia, Spain, and Italy – users have been locked out by a program that demands $300 USD in Bitcoin per computer. The attack appeared to exploit a vulnerability purportedly identified for use by the U.S. National Security Agency and later leaked to the internet.
How it works
According to Jakub Kroustek of the computer security firm Avast, “The ransomware changes the affected file extension names to “.WNCRY”, so an infected file will look something like: original_name_of_file.jpg.WNCRY, for example. The encrypted files are also marked by the “WANACRY!” string at the beginning of the file.”
In addition, Kroustek states the ransomware places the following on infected computers:
Ransom Note – A simple text file with instructions for paying the ransom.
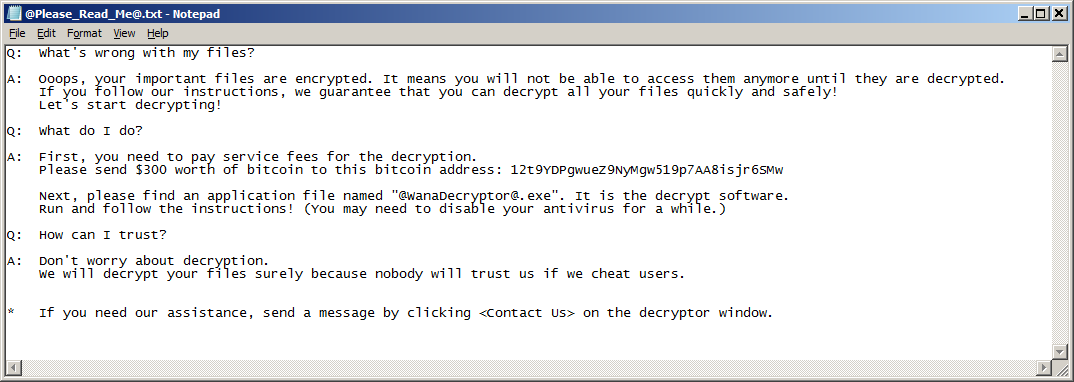
(Screenshot courtesy of Jakub Kroustek)
Wana Decrypt0r 2.0 – A program is installed on the host computer with instructions on how to pay the ransom with bitcoin, an explanation of what happened, and a countdown timer.
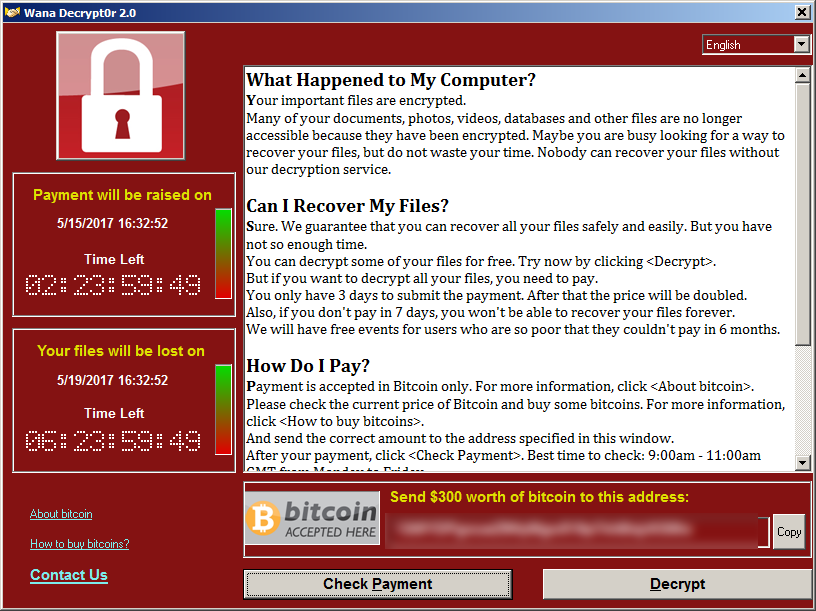
A ransomware program that locks the users computer and gives instructionson how to pay the ransom.
Wallpaper – Additionally, the victim’s wallpaper is changed to the following image, which repeats instructions on how to pay the ransom.
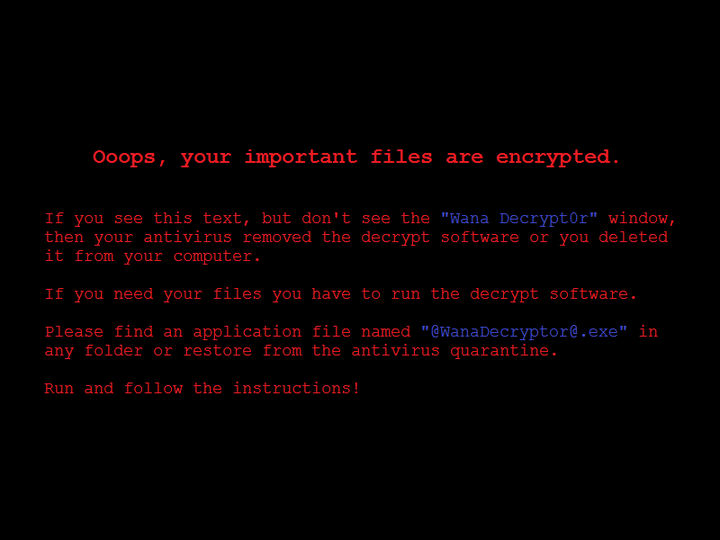
(Screenshot courtesy of Jakub Kroustek)
The attack hit Britain’s health service, forcing affected hospitals to close wards and emergency rooms. Related attacks were reported in Spain, Portugal and Russia. Two security firms — Kaspersky Lab and Avast — said they had identified the malware behind the attack in upward of 70 countries, although both said the attack has hit Russia hardest.
Reports are also coming from Spain that telecom Telefonica is experiencing the same type of ransom screen pointing to the same bitcoin address:
Ransomware that hit #Telefónica and NHS pointing to same Bitcoin address and already receiving payments #nhscyberattack pic.twitter.com/eUtX7VsnRt
— Jorge Blasco (@guizos) May 12, 2017
Hospitals in areas across Britain found themselves without access to their computers or phone systems. Many canceled all routine procedures and asked patients not to come to the hospitals unless it was an emergency. Some chemotherapy patients were even sent home because their records could not be accessed.
Most of the affected hospitals were in England, but several facilities in Scotland also reported being hit. Doctors’ practices and pharmacies reported similar problems.
As similar widespread ransomware attacks were reported in China, Spain, Romania and elsewhere, experts warned that online extortion attempts by hackers are a growing menace. Hospitals, with their often outdated IT systems and trove of confidential patient data, are a particularly tempting target.
British Prime Minister Theresa May said there was no evidence that patient data had been compromised in the attack, and that it had not specifically targeted the National Health Service.
“It’s an international attack and a number of countries and organizations have been affected,” she said.
Alan Woodward, visiting professor of computing at the University of Surrey, said there was evidence the ransomware was spreading using a Microsoft flaw exposed in a recent leak of information from U.S. intelligence agencies.
He said the affected computers likely had not applied the Microsoft patch or were running old operating systems for which no patch was available.
“I don’t believe it will have been a targeted attack, but will simply have been that the ransomware has sought out those organizations that are running susceptible devices,” he said.
NHS Digital said the attack “was not specifically targeted at the NHS and is affecting organizations from across a range of sectors.” It initially said 16 NHS organizations had reported being hit, and more reports came in as the day went on.
Spain, meanwhile, activated a special protocol to protect critical infrastructure in response to the “massive infection” of personal and corporate computers in ransomware attacks. The National Center for the Protection of Critical Infrastructure says Friday it was communicating with more than 100 providers of energy, transportation, telecommunications and financial services about the attack.
The Spanish government said several companies had been targeted in ransomware cyberattack that affected the Windows operating system of employees’ computers. It said the attacks were carried out with a version of WannaCry ransomware that encrypted files and prompted a demand for money transfers to free up the system.
Bart’s Health, which runs several London hospitals, said it had activated its major incident plan, cancelling routine appointments and diverting ambulances to neighboring hospitals.
Patrick Ward, a 47-year-old sales director, said his heart operation, which was scheduled for Friday, was cancelled at St. Bartholomew’s Hospital in London.
The National Cyber Security Centre, part of Britain’s GCHQ electronic intelligence agency, said it was working with police and the health system to investigate the attack.
British government officials and intelligence chiefs have repeatedly highlighted the threat to critical infrastructure and the economy from cyberattacks. The National Cyber Security Centre said it had detected 188 “high-level” attacks in just three months.
Story includes reporting from The Associated Press and Peoples Daily, China.
 CGTN America
CGTN America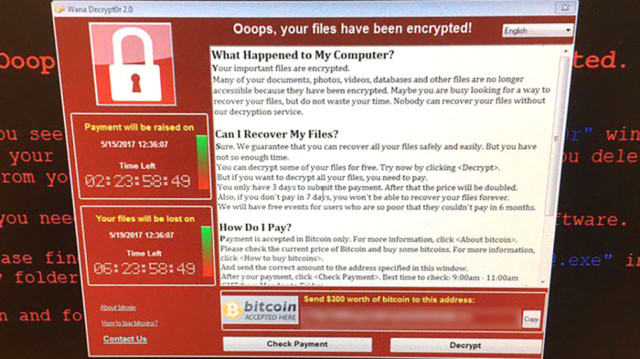 Screenshot of a hacked NHS computer demanding bitcoin ransom for access to its files. (PHOTO: @zerohedge via Twitter)
Screenshot of a hacked NHS computer demanding bitcoin ransom for access to its files. (PHOTO: @zerohedge via Twitter)
